POCKETALK Sentio White Paper
POCKETALK Sentio White Paper
Version 1.0 (Revised: 11th March, 2025)
POCKETALK
1.Introduction
This document is intended for those who are considering using or are currently using POCKETALK Sentio (hereinafter referred to as “Sentio”). It aims to provide information about our company’s (hereinafter referred to as “we”) security initiatives regarding customer personal data (hereinafter referred to as “customer data”) that we hold, and to help you understand the precautions for using Sentio safely. This document also serves as an appendix to the Terms of Use and constitutes an agreement between us and the customer regarding the use of Sentio.
2.About Cloud Service Providers
The Sentio Cloud is developed, operated, and provided to customers by us using Google Cloud Platform (hereinafter referred to as “GCP”).
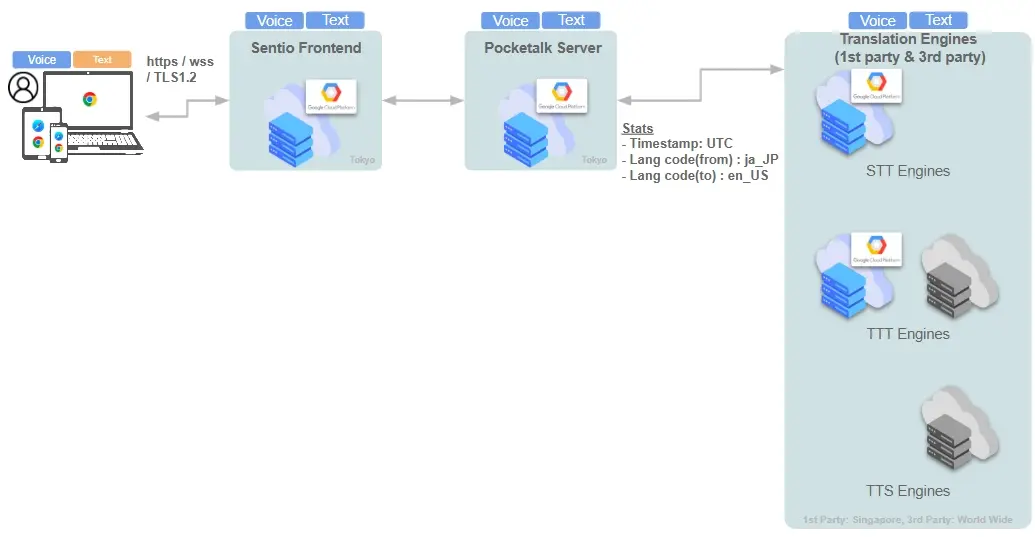
<Sentio – User and System Relationship Diagram\_Serial Code Auth>
3.Division of Responsibilities Between Us and Customers
The following diagram explains the division of responsibilities between us and customers when using Sentio.
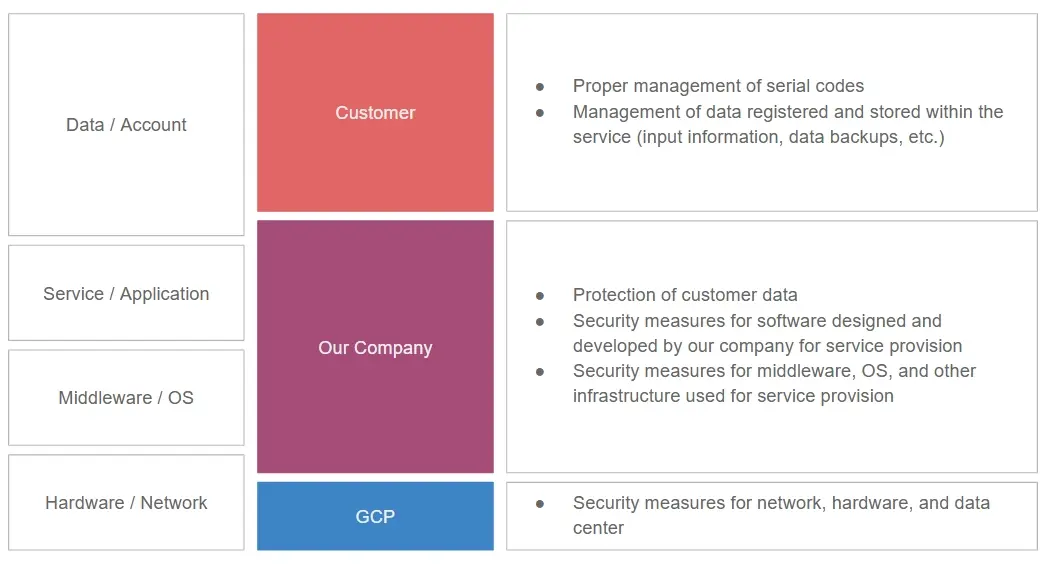
<Sentio | Division of Responsibilities Between Us and Customers>
4.Data Storage Location
GCP and AWS used in Sentio are operated in the following regions:
- GCP
- Region: Asia Northeast
- Multi-AZ: 2 locations within Asia
5.Service Level Objectives (SLO)
| Service hours | 24 hours a day, 365 days a year ** We also monitor the service during the same time period. |
|---|---|
| Service availability | 99.0% **Does not include annual planned service outages |
| Planned service outages | 2~4 times / year ** Service outages are expected to last up to 6 hours at a time. |
| Data backup | The DB configuration is redundant with a primary / secondary configuration (constantly synchronized). Data generation management backup is not provided. |
6.Our Safety Management Measures
We strive to design, build, and operate appropriate information security and data security both internally and with our business partners so that customers can use our services with peace of mind and safety.
Policies for Information Security
We have established the “Basic Information Security Policy” and “Basic Cloud Service Security Policy” as the basic policies for our information security initiatives in cloud services, and we operate our services in accordance with these policies.
Roles and Responsibilities for Information Security
We have established the “Basic Information Security Policy” and “Basic Cloud Service Security Policy” as the basic policies for our information security initiatives in cloud services, and we operate our services in accordance with these policies.
Communication with Relevant Authorities
Communication with relevant authorities is as defined in “4. Data Storage Location”.
Sharing and Division of Roles and Responsibilities in the Cloud Computing Environment (CLD.6.3.1)
The sharing and division of roles and responsibilities in the cloud computing environment are as defined in “3. Division of Responsibilities Between Us and Customers”.
Improving Information Security Awareness, Education, and Training
We promote the importance of information security throughout the company and regularly conduct necessary education and training.
Asset Inventory
We identify and appropriately manage information, other assets related to information, and assets related to information processing facilities.
Removal of Cloud Service Customer Assets (CLD.8.1.5)
The handling of customer data when a customer terminates the use of the service is described below.
-
Customers cannot apply for service termination by themselves from the functions provided by Sentio. For customers who wish to terminate the service, please contact the following contact points.
Contact Information
North American customers: https://pocketalk.com/contact-us
European customers: https://pocketalk.com/en_eu/contact-us
Asian customers: https://pocketalk.link/inquiry -
If you need the history data of the interpretation by Sentio, please download it from Sentio at your own responsibility and store it appropriately. (However, it is necessary to turn ON the download setting of the interpretation history by the operation on Sentio. For details, please refer to the manual.)
Labeling Information
Sentio does not provide a function to label the name of customer information or terminal information because there is no registration information.
User Registration and Deletion
Sentio uses serial code authentication for service usage. Serial codes can only be issued by our company, and customers cannot issue them themselves. Please contact our company for the issuance of new serial codes.
Providing User Access
Sentio uses serial code authentication to use the service. Serial codes can only be issued by us, and customers cannot issue them by themselves. Please contact us for issuing new serial codes and deleting them.
Managing Privileged Access Rights
Sentio does not have privileged access rights.
Management of User Secret Credentials
The management of serial codes is as defined in “3. Division of Responsibilities Between Us and Customers”.
Restricted Access to Information
Sentio does not limit the information displayed or the functions available for each serial code.
In addition, Sentio has a function to share the translation result with a specified shared device (hereinafter referred to as the “sharing function”). When the sharing function is used, a URL is issued, and the translation result can be viewed by accessing the URL from the shared device. The shared device can only view the translation result, and cannot re-share it. Also, the translation result is not stored on the shared device or in the cloud at all.
For details, please refer to the manual.
Use of Privileged Utility Programs
Sentio does not provide utility programs such as APIs that bypass security procedures and enable the use of various service functions. For privileged utility programs necessary for service provision in our company, we strictly limit users, confirm the validity of use in advance, acquire logs, and conduct reviews.
Separation in Virtual Computing Environment (CLD.9.5.1)
It operates in a multi-tenant environment and controls access to other tenants.
Fortification of Virtual Machines (CLD.9.5.2)
All virtualized environments to be constructed restrict ports and protocols to block unauthorized access. In principle, vulnerability diagnosis and penetration tests by a third-party organization are conducted once a year.
Policy on the Use of Management Measures by Encryption
Data stored on the device is encrypted using AES, with key management handled within browser storage. Communication is encrypted using SSL/TLS (supporting TLS 1.2) communication.
Change Management Procedure
When updating or performing regular maintenance of the services provided, we will notify you in advance by email.
Capacity/Ability Management
In order to provide stable service, we monitor the resources of each server and increase capacity as needed.
Security of Operations of Business Administrators (CLD.12.1.5)
The operation method and security setting operation of Sentio are explained in the manual.
In our operation business, the cloud environment is managed separately for staging and production, and access is permitted only to limited business personnel. Access to and operations performed on the production environment are stored in the audit log. This access restriction is managed by GCP’s IAM, and IAM user inventory is regularly performed and managed appropriately.
Information Backup
The DB configuration is redundant with a primary/secondary configuration (constantly synchronized).
Since we do not store any data about customers, we do not back up data by generation.
Event Log Acquisition
Sentio does not provide a function for customers to acquire event logs by themselves, but we acquire and store appropriate logs (for 90 days) necessary for service maintenance and management.
If an important incident occurs and log information etc. is required for the purpose of actual investigation, we will conduct an investigation from the access log for the past 90 days according to the customer’s inquiry, so please contact privacy@pocketalk.com.
Clock Synchronization
Sentio synchronizes time (UTC) by unifying with the internal NTP server provided by GCP.
Cloud Service Monitoring (CLD.12.4.5)
We monitor the resource status related to the system such as CPU, memory, and disk usage rate.
We also monitor the service to see if the Sentio web application is operating normally.
Management of Technical Vulnerabilities
We collect vulnerability information, and if it becomes necessary to respond within the scope of our responsibility, we will implement countermeasures in regular or emergency maintenance.
Maintenance information will be notified by email.
In order to ensure even greater security, we establish security requirements at the time of development design, and perform not only in-house testing but also vulnerability diagnosis and penetration testing by third-party organizations before release.
Network Separation
Access to Sentio is done through the Internet line.
In our maintenance and operation business for the production environment, we appropriately manage authority with GCP’s IAM, and permit access after application and approval. In addition, access to the production environment and operations performed are managed by storing them as audit logs.
Analysis and Specification of Information Security Requirements
We maintain and provide the information security required by customers under the Basic Information Security Policy and the Basic Cloud Service Security Policy.
As the specifications of the information security functions mainly considered by customers, this document describes the following items.
- Access restriction function (restriction of access to information, fortification of virtual machines)
- Communication encryption function (policy on the use of management measures by encryption)
- Backup function (information backup)
Policy for Security-Conscious Development
As a security-conscious development policy, we address security risks and vulnerabilities from the development stage, and conduct vulnerability diagnosis and penetration testing by third parties at the time of release.
Security Handling in Supplier Agreement
The roles and responsibilities in Sentio are defined in the Terms of Use and services are provided. Regarding the responsibility demarcation point of this service, please refer to “3. Division of Responsibilities Between Us and Customers”.
ICT Supply Chain
We grasp the information security level of the cloud service provider used by our company, and confirm that it is consistent with our information security.
Sentio is operated with GCP as a cloud service provider.
For the compliance status of GCP, please refer to the following.
https://cloud.google.com/compliance
Responsibilities and Procedures
If a security incident (data loss, long-term system shutdown, etc.) that has a significant impact on Sentio users occurs, we will notify you by email within 72 hours in principle. For inquiries regarding security incidents, please contact privacy@pocketalk.com.
Reporting of Information Security Events
We will notify customers by email.
For individual inquiries, please contact privacy@pocketalk.com.
Collection of Evidence
If a legitimate disclosure request based on law is made, such as a disclosure request from a court, customer data may be disclosed to the relevant organization without customer’s consent. If an important incident occurs to the customer and log information etc. is required for the purpose of actual investigation, we will conduct an investigation from the access log for the past 90 days according to the customer’s inquiry, so please contact privacy@pocketalk.com.
Identification of Applicable Laws and Contractual Requirements
The “governing law” applicable to the use of Sentio is “Japanese law”.
We strive to legally comply with various laws and regulations related to Sentio operation in accordance with the related laws and regulations management guidelines.
Intellectual Property Rights
Intellectual property rights are defined in the Terms of Use.
Protection of Records
For details on protection of records, please refer to “Event Log Acquisition”.
Regulation on Encryption Function
For the use of encryption, please refer to “Policy on the Use of Management Measures by Encryption”.
Sentio does not utilize encryption technology subject to export regulations.
Independent Review of Information Security
We conduct internal audits and management reviews to maintain and improve information security.